Identity¶
API - CLI Identity Credential Types¶
For access via CLI/API, OpenStack offers different options depending on the implementation, which are more suitable for the specific requirements. Currently, the following credential types are available.
A) Application Credentials
Keystone Application credentials allow users to generate their own OpenStack credentials that are appropriate for applications and authenticate to the Identity Service without having to disclose their primary credentials.
Advantages: Application credentials can be easily revoked or changed without interrupting the application, or they can even have an automatic expiration time.
Disadvantage: You are bound to the user account that creates the application credentials. If an employee leaves the company, it is not enough to deactivate the user account. His application credentials must also be deleted. More about application credentials see create_application_credentials.
B) Local User - API access via Local Keystone password is not supported.
C) Download current user’s session token (NEW) - Users who have activated OTP (2 Factor - OneTimePassword) can now easily download the current User Session Token, which is valid for 24 hours, via the OpenStack© Management Portal (Horizon).
To do this, log on to the OpenStack© Management Portal (Horizon).
Then click on the small arrow in the upper right corner and select Export credentials
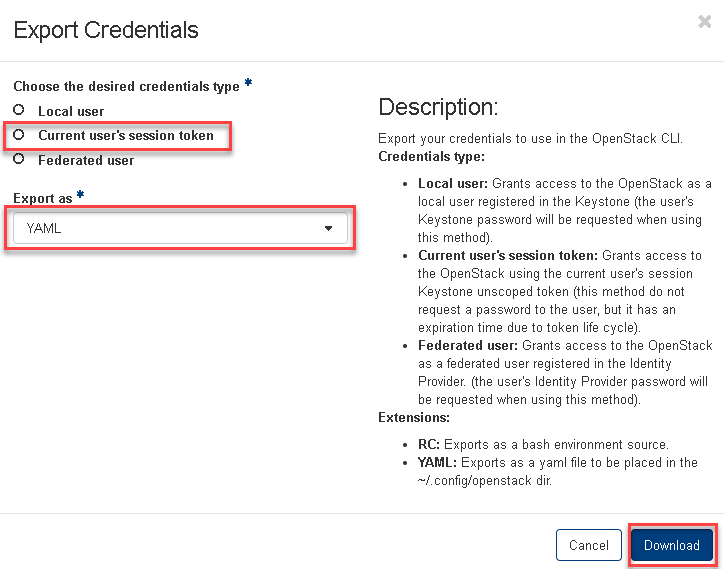
In the next window select Current user’s session token and the desired export format (YAML or RC) and confirm with Download
Note
RC: Exports the bash environment variables as source file.
YAML: Is exported as a yaml file, which must be stored in the directory ~/.config/openstack and can then be used via the environment variable OS_CLOUD or the CLI parameter –os-cloud
Tip
The “Current user’s session token” is valid for 24 hours and can be used for the API, the CLI or Terraform. After that the token expires and the user can get a new token via Horizon.
D) Federated user
Users who have not activated OTP can also select the **Federated user method for both methods A) and C) and will then be asked for their Keycloak password when an API / CLI call is made. Terraform does not support this method.
Note
Depending on the defined password policy it is possible that not all credential types are allowed. For example, if OTP is mandatory, then the credential type D) Federated user is currently not possible.
How to create Application Credentials¶
The Federated Login Credentials of a user cannot be used in the Openstack for the access from a CLI tool. The solution to this problem are Keystone Application Credentials, which the user can create after logging in to the OpenStack portal and then use directly for CLI tools.
Application credentials allow users to generate their own OpenStack credentials that are appropriate for applications and authenticate to the Identity Service without having to disclose their primary credentials.
Application credentials can be easily revoked or changed without interrupting the application, or they can even have an automatic expiration time.
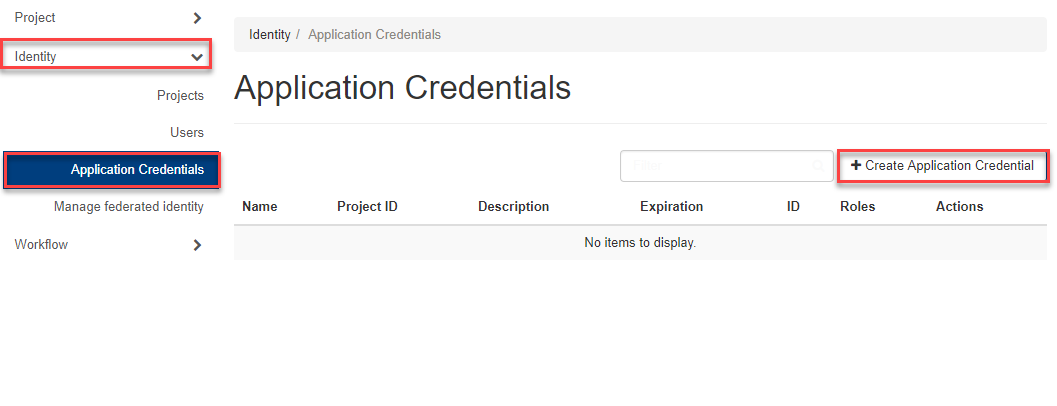
In the OpenStack Portal, please navigate to Identity => “Application Credentials” and click on Create Application Credentials
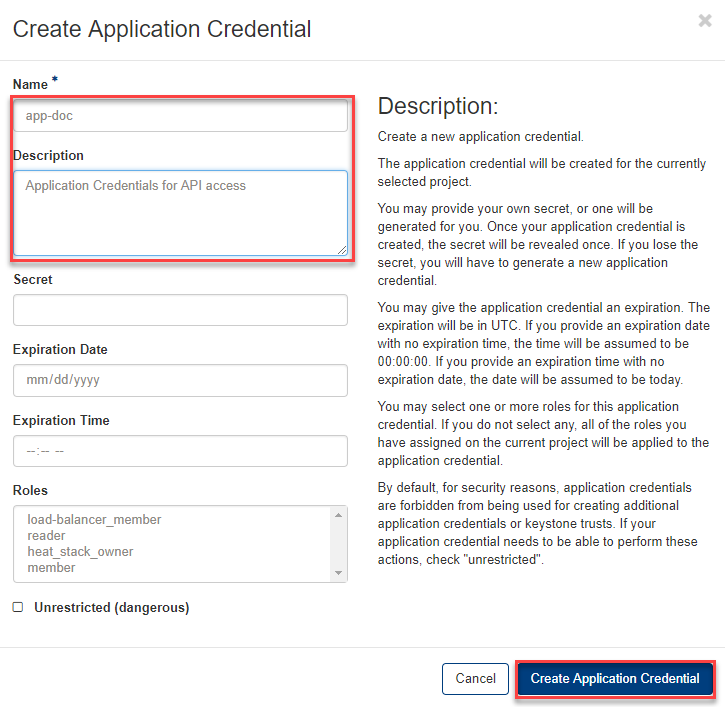
Enter a name and description of the Application Credential and click on “Create Application Credential”.
- The application credentials are created for the currently selected project.
- You can specify your own secret, otherwise one will be generated for you.
- Optionally, you can provide the application credential with an expiration date and time.
- You can select one or more roles for these application credentials. If you do not select any, all roles you have assigned in the current project will be applied. For more information on roles, see appcredential-roles.
Important
If you need the application credential to create a Kubernetes cluster, you need to check “Unrestricted (dangerous)” to get the necessary permissions (creation of additional trusts).
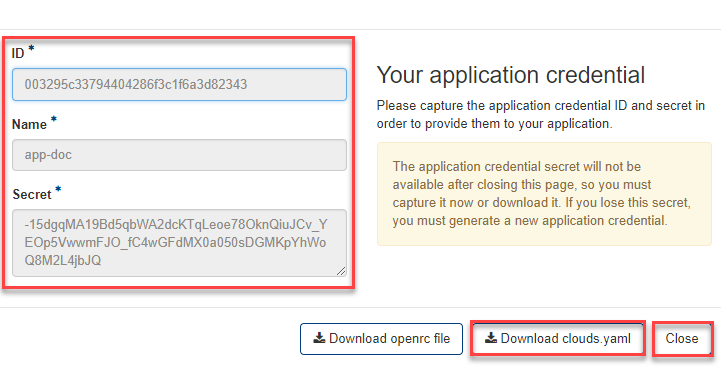
- Please make a note of the ID and the Secret of the created Application Credentials in order to use them in your CLI tool.
- Alternatively you can download “clouds.yml” or “openrc” (Legacy) file, which contains all information, depending on your later use.
Important
The Application Credential Secret is no longer available after closing this page, so you need to note it down now or download the clouds.yaml file! If you lose this, you must generate a new Application Credential.
- Then click on “Close” and you’re done
Example of a cloud.yaml file
# This is a clouds.yaml file, which can be used by OpenStack tools as a source
# of configuration on how to connect to a cloud. If this is your only cloud,
# just put this file in ~/.config/openstack/clouds.yaml and tools like
# python-openstackclient will just work with no further config.
# If you have more than one cloud account, add the cloud entry to the clouds
# section of your existing file and you can refer to them by name with
# OS_CLOUD=openstack or --os-cloud=openstack
clouds:
openstack:
auth:
auth_url: https://keystone.service.ewcs.ch/v3
application_credential_id: "003295c34794404226f3c1f6a3d82143"
application_credential_secret: "-15dgWMA19Bd5qbWA2dcKTqLeoe78OknQiHJCv_YEOp5VwwmFJO_fC4wGFdMX0a050sDGMKpYxWoQ8M2L4jbJQ"
region_name: "ch-zh1"
interface: "public"
identity_api_version: 3
auth_type: "v3applicationcredential"
The selectable roles in Application Credentials mean:
| Role | Description |
|---|---|
| _member_ | Default role that allows access to a Project |
| member | Duplicate of _member_ still needed for some API calls |
| heat_stack_owner | Role is allowed to create/start heat stacks |
| reader | can read Secrets in Barbican |
| creator | may create Secrets in Barbican |
| load_balancer_member | May create loadbalancer |